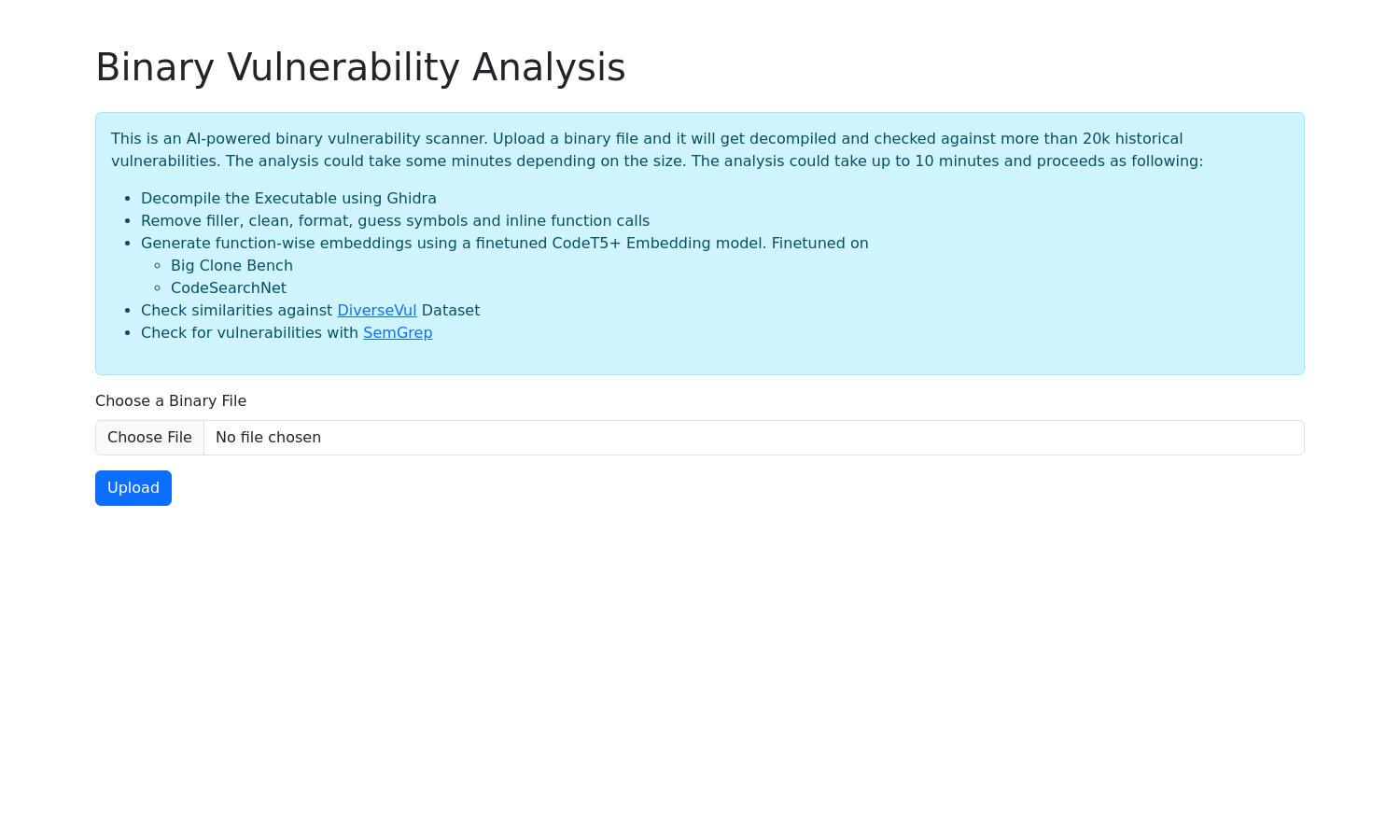
Binary Vulnerability Analysis
About Binary Vulnerability Analysis
Binary Vulnerability Analysis offers an advanced AI-powered scanner for identifying vulnerabilities in binary files. It performs a thorough analysis by decompiling executables, generating embeddings, and comparing against extensive databases. Ideal for developers and security professionals, this tool enhances software security, making it a must-have for vulnerability management.
Binary Vulnerability Analysis supports a range of pricing plans tailored for individuals and businesses. Options include a free tier for casual users and premium plans that offer advanced features and faster analysis. Upgrading allows access to enhanced capabilities, making it worthwhile for frequent users seeking robust security solutions.
The user-friendly interface of Binary Vulnerability Analysis is designed for seamless navigation, allowing users to efficiently upload and analyze binaries. With an intuitive layout, users can easily access features and understand the results. This design promotes a smooth user experience, making vulnerability scanning straightforward and effective.
How Binary Vulnerability Analysis works
Users engage with Binary Vulnerability Analysis by simply uploading their binary files to the platform. The system then decompiles the executables using advanced tools, cleans the code, and generates embeddings. After processing, it checks for vulnerabilities against historical datasets, ensuring users receive detailed, actionable insights to enhance their software security.
Key Features for Binary Vulnerability Analysis
AI-Powered Vulnerability Scanning
The AI-Powered Vulnerability Scanning feature of Binary Vulnerability Analysis revolutionizes how users detect vulnerabilities by applying advanced machine learning models. This innovative approach ensures thorough evaluations against extensive databases, empowering users to identify and rectify security risks effectively in their binary files for optimal safety.
Ghidra Decompilation Process
The Ghidra Decompilation Process utilized by Binary Vulnerability Analysis stands out for its ability to accurately transform binaries into readable formats. This feature enhances users' understanding of their code, making it easier to identify vulnerabilities and improve overall software security through detailed insights and effective remediation strategies.
Function-wise Code Embeddings
Binary Vulnerability Analysis incorporates Function-wise Code Embeddings, which uniquely analyze code segments by generating contextual representations. This feature facilitates precise vulnerability detection by comparing embeddings across historical datasets, enabling users to swiftly identify potential security threats and enhance their binary files’ safety and performance.